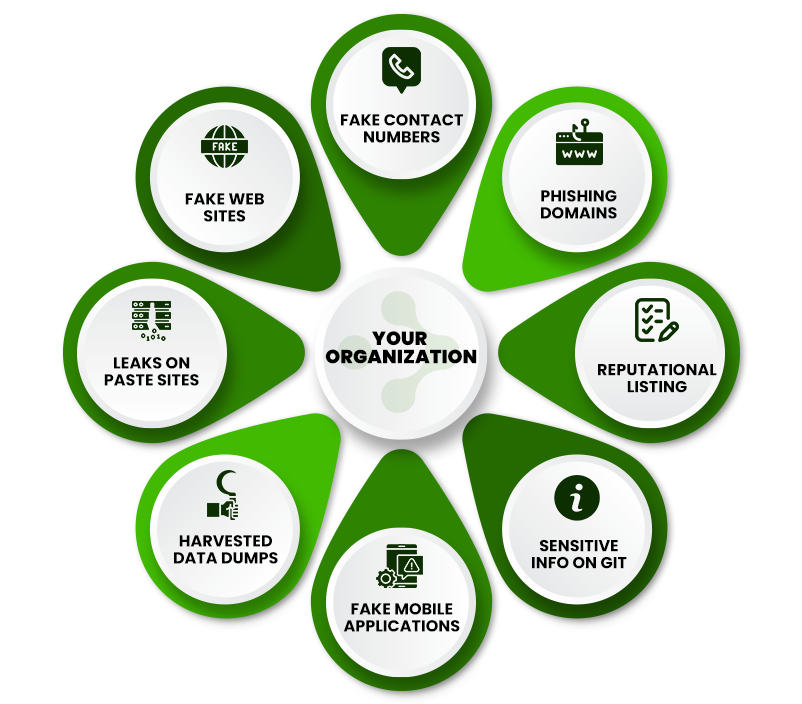
External Threat Sources
- Unauthourized Extended surface finder.
- Primary intel of upcoming attack.
- Counter-Intelligence hunting on dark web
- Event trapping for the organization.
Threat Actors, Sources and Infrastructure
- Specific sources are established by malicious actors
- These sources are targeted against your company
- They cause brand damage to your organization
- They are also used for launching attacks
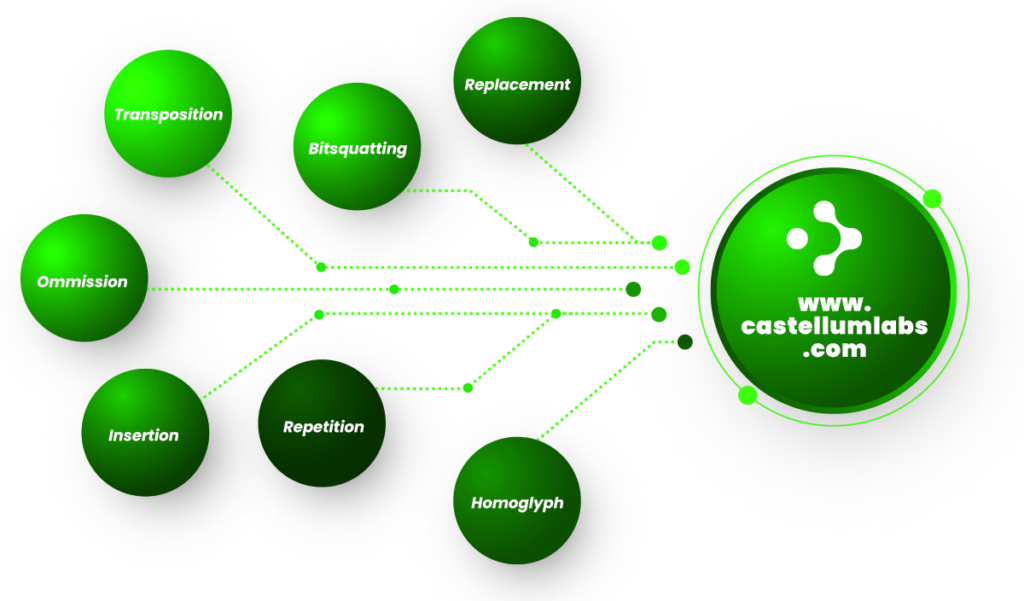
Phishing Domains Targeting
- Large Number of Specific Phishing Domains are registered every month
- Hackers create these domains, to target specific organization
- Domains are similar to your company & brand name
- Well design phishing campaigns are launched from these domains
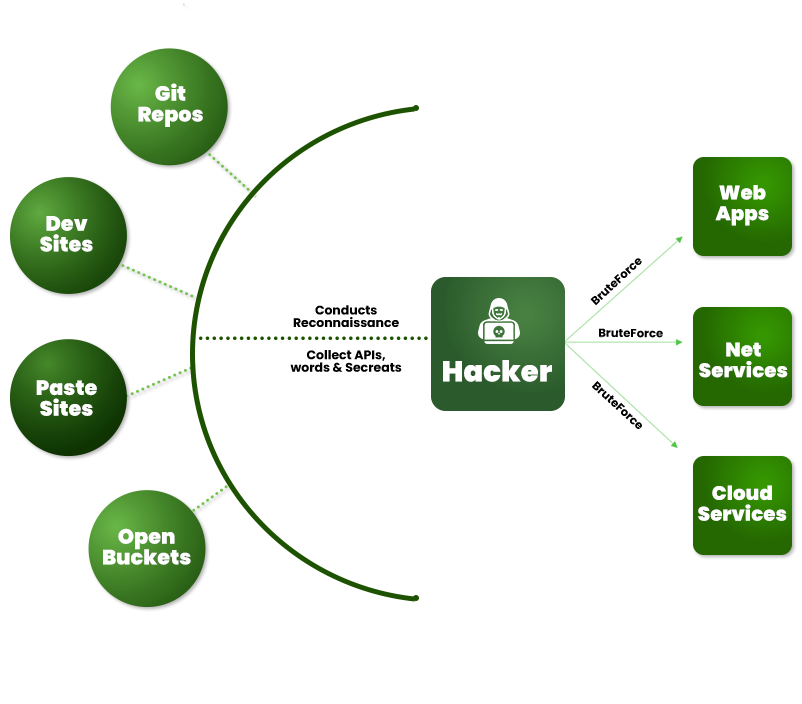
Leakages with Sensitive Data
Hackers usually find
large number of API Keys,
Credentials on GitHub
Developers use paste sites
for collaboration, and
leave sensitive info there
Forums which are used
for discussion on code, also
have a lot of sensitive info
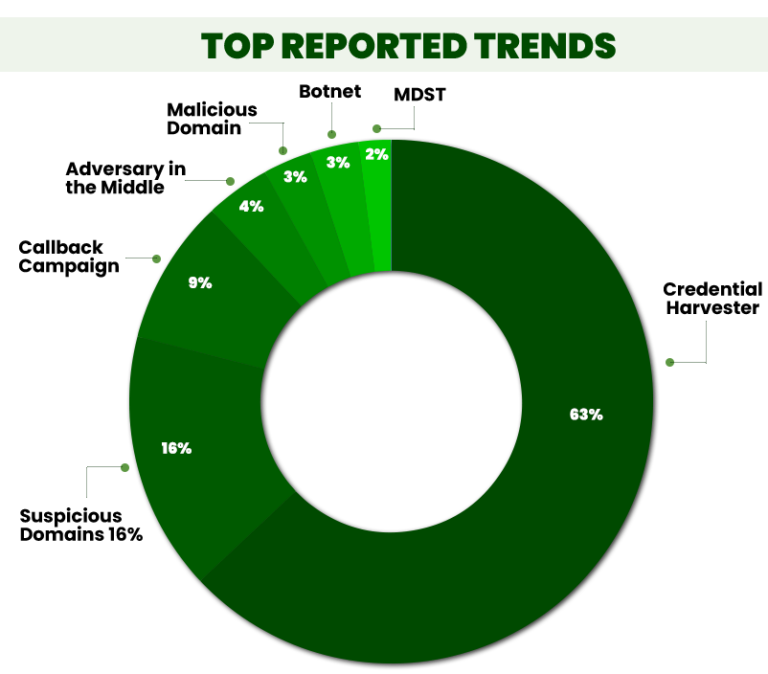
Credential Harvesting
"Large number of credentials are harvested by hackers and darkweb
operators, which in turn are used by attack groups, to launch large
scale brute force attacks against organizations world over"
Fake Sites and Applications
- Fake Mobile Applications have flooded marketplaces
- These fake applications defraud your customers
- And, they are also used to steal company data

Hacker's Reconnaissance of You !

find out more
External Threat Sources
Simplifies your Monitoring
Reimagining Cyber Security for NextGen Threats !
- Gather information about potential threat sources.
- Analyse, refine and analyse information to mitigate attacks.
- Use cybersecurity mechanism to lure away the threats.
- Anticipate for upcoming attacks and neutralise them.
Get started today!
To know more and to setup an experiential demo
