
A Brief Guide of Threat Hunting Techniques
Threat hunting is an important component of security operations center services that should be implemented as soon as possible. Threat hunting is the skill of detecting unknowns in the environment, extending beyond typical detection systems like SIEM, EDR, and others. Hunting can be done in a variety of ways, and your team can choose the one that best suits your needs.
What is Threat Hunting, exactly?
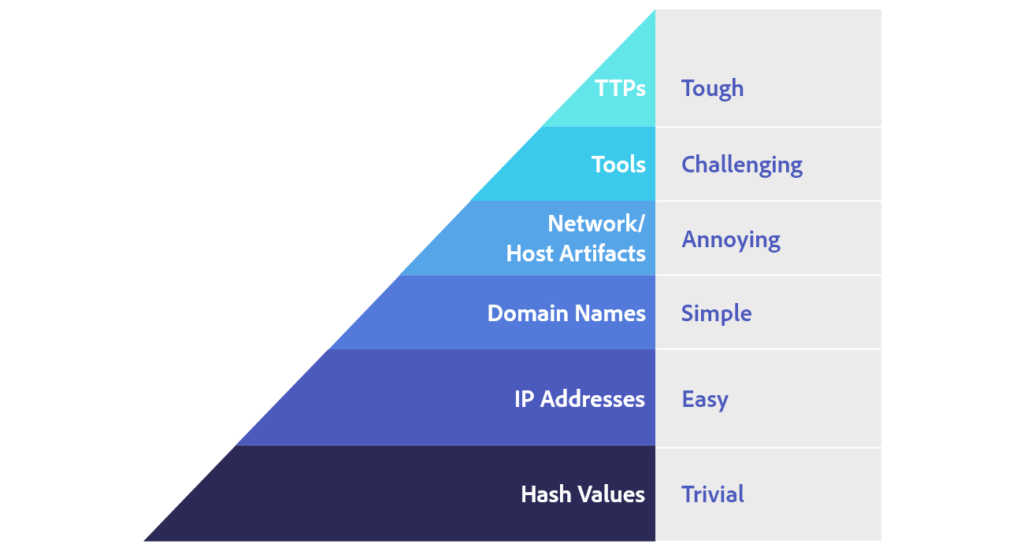
The Pyramid of Pain by David Bianco demonstrates how threat hunting should be carried out to guarantee that threat actors are noticed, identified, and isolated before they impact the environment.
Types of Hunting
The environment’s fecundity is crucial to a successful search. SIEM and EDR tools are commonly used by hunters as the foundation for their hunts. They can also use other tools to conduct network-based hunts, such as packer analyzers.
SIEM and EDR technologies, on the other hand, demand that all of your environment’s “crown jewels” be interconnected. This ensures the use of an indicator of attack (IoA) and an indicator of compromise (IoC) in the hunt.
What Are Your Hunting Grounds?
Structured Hunting:
An attacker’s IoA and tactics, methods, and procedures (TTPs) are used to create a systematic hunt. All hunts are coordinated and based on the threat actors’ TTPs. As a result, the hunter is usually able to spot a threat actor before the attacker has a chance to harm the ecosystem. This type makes use of both PRE-ATT&CK and corporate frameworks to implement the MITRE Adversary Tactics Techniques and Common Knowledge (ATT&CK) framework.
Unstructured Hunting:
A trigger starts an unorganized hunt. It’s more akin to intelligence-based hunting, where any of the IoCs could be the trigger. This is usually when a hunter begins looking for pre- and post-detection trends. The hunter can go back as long as data retention and previously linked offenses permit. This research informs the hunter’s approach.
Models of Hunting
Intel-based Hunting:
This is a model for reactive hunting. The IoCs from threat intelligence sources are used as inputs. The hunt then follows the SIEM and threat intelligence’s specified guidelines.
IoCs, hash values, IP addresses, domain names, and networks, as well as host artifacts provided by intelligence sharing platforms like computer emergency response teams, are used in intelligence-based searches (CERTs). As Structured Threat Information eXpression (STIX) and Trusted Automatic Exchange of Intelligence Information, an automated alert can be exported from these platforms and imported into the SIEM (TAXII). The threat hunter can study the activities before and after the alert to find any compromise in the environment once the SIEM has received the alert based on an IoC.

Hypothesis hunting using a threat hunting library:
This is a paradigm of proactive hunting. It uses global detection playbooks to identify advanced persistent threat groups and malware attacks, and it is aligned with the MITRE ATT&CK methodology.
The IoAs and TTPs of attackers are used in hypothesis-based hunts. To build a hypothesis in accordance with the MITRE framework, the hunter identifies threat actors based on the environment, domain, and attack tactics used. Once a pattern has been found, the threat hunter watches for it in order to detect, identify, and isolate the threat. As a result, the hunter is able to locate threat actors ahead of time, before they do environmental damage.
Custom Hunting:
This approach is based on situational awareness and hunting techniques used in the industry. It detects anomalies in SIEM and EDR tools and is fully customisable to meet customer needs.
Customers’ requests or situations, such as geopolitical crises and targeted attacks, are the basis for specialized or situational hunts. Using IoA and IoC information, these hunting activities can use both intel- and hypothesis-based hunting models.
Hunting Frameworks
Threat hunting frameworks can be used in a variety of ways by businesses. The following are two of the most common:
Threat Intelligence is included into the Targeted Hunting framework:
This framework is designed for hunting based on intelligence. Threat intelligence, past incidents, red teaming actions, and other sources provide triggers.
The MITRE PRE-ATT&CK and ATT&CK frameworks:
These frameworks have a knowledge base that may be used to counter certain adversary threat models and tactics.
A threat hunting team’s backbone is built by combining these tactics and resources as needed.




Leave a comment: