
Wondering whether your credentials are exposed on the Dark Web?
During the last few weeks, one constant question, I had to answer,
While demoing and/or discussing one of our portfolio service which is for watching threats on dark web and external places, with CISOs and Security Professionals, was.
I think this question/curiosity, comes from a mindset, which has following presumption about darkweb and something outside.

- Something which is already on darkweb, there is not much which can be done as an action or as prevention measure
- Wouldn’t it be better, if breaches and leaks are stopped in the first place, than, go looking for them, once they are out there on dark web or other places
- It will be only an embarrassment and not serve any real purpose, to find out, if there is a leak or stolen data about my org has been found on dark web or on social media
- Is there anything concrete which I can do, when and if, I find information leakage or any other threat data specifically for my organization outside, in dark web or other places?
While questions are genuine, “Stark Reality of Today’s Threat Landscape and Posture” demands a perspective and view, which goes beyond traditional lock-and-latch and also beyond detect-and-respond using a host of in-house/in-enterprise security apparatus and tools.
Before I talk about what can be done, with “Dark Web Monitoring”, following key points need to be understood, and, may be delve into…

- Breach will happen sooner or later
- Detection and response is key to protection
- Best of the best solutions will sometime fail in fortifying my enterprise
With the above mentioned “Major Security Paradigm Change” perspectives…
Let’s understand what data is leaked or lost or stolen or breached from your enterprise. Some of this could exist, even without a breach or active stealing/leaking of data. There could be dozen of different categories, but, for simplicity, I will keep following significant/top-level categories.
- Reconnaissance Data
- Credentials and Mail Access
- Customer Data (Personal and Financial Data)
- Company Confidential (Intellectual Property) Data
- Internal Systems and Network Details (Including Access Elements)
- Reputational Data and Malicious Conversation
Though specifics of the action, one could take on finding data/info from darkweb or other external sources, but, a general list of things, an organization can potentially do, is, following.
Concealing Sensitive Info / Blocking the Leak
In many scenarios leak takes place from an internal source, which is in control of orgs, and, simple operational measures will ensure that no unauthorized people can get an access to the sensitive information. Leakages from web-site or portals or sometime through internal mails are example of this. In an average period of 3 years an org ends up leaking information data from its own sources, because of operational issues or data flow/access issues.

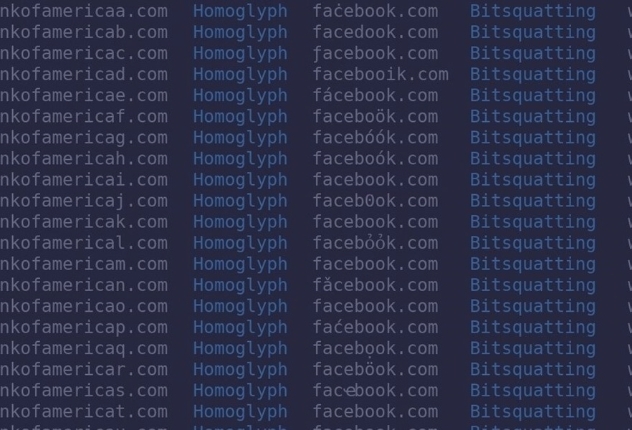
Blocking and Preventing
If the data, which has been lost, is of nature, which can be simply blocked and placed on a restriction rule set, then, a simple security operation can take care of things. One, simplest example of this would be phishing sources, discovered by you and your threat intelligence provider, such as domain names suspicious of phishing sources, which seem like your own domain name.
Credential Changes
A lot of what is discovered on darkweb, is credential dumps or password dumps. This has taken a proportion, that, a continuous program model approach is needed in organizations. They need to look for potential credential leak or compromise and its availability on dark-web, and, then organize a password change or sometime identity changes within organization.
This is usually a tough one, because, a lot of time, organizations can bump into large set password dumps, which are claimed to be for their organization, with no concrete way of ensuring they indeed belong to their staff.

Employee Mail ID Compromise Data
Sometime organizations will find that their employees used company’s mail ID, on external sites, without permission and/or required authorization. Then organization can further learn that, sites, on which employee had used his company mail ID, has been compromised. This usually means, employee has had his credentials stolen, from that site.

This issue usually does not seem much of a threat, but, this in fact poses, maximum threat to organizations. Among all the breaches, this one, which usually gets completely unnoticed & sometime this is the one which gets “no prevention/response and/or action” by an enterprise, despite the knowledge about breach.
Ideally an organization should do a periodic review of reported breaches on pawned sites, &, then use that data, to enforce a password change & caution employees to not to use company mail ID, without company’s knowledge, on external sites/platforms/SaaS.
Make Data Useless
This is probably the most important and most required action needed, when you are looking at customer data, specifically financial one, reported from / on darkweb. Here, your ability to protect customer interest, depends on
- Your ability to find out if your data made its way to darkweb
- And, your swift action on making this data useless through specific action
A lot of time making this data useless for a cyber criminal is not a simple exercise. It needs a coordinated exercise, which other than work on data repositories (and action on data), needs things which include customer communication, and, a lot more.
Breach Reporting/Disclosure Preparedness
Quite a many times, an enterprise will get to know about their lost or breached data, through media or security experts or cyber crime investigative journalists. And, whenever such thing happens, a messy and arduous process follows up.
If the organization has some measures in place, to get to know about leak of their data on darkweb or social web, there is a lead time they get to prepare for breach response/report.
The nature, urgency and sometime even the extent of response depends on,
- How the breach was reported?
- Who reported the breach?
If organization has placed dark web monitoring process, and, has a well defined breach handling process, the possibility is, organization will have much better handling of the breach, than, the one which gets reported through/by media.
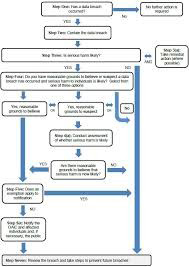
Legal Options/Process
There are two kind of breaches which usually warrant an organization to take legal and forensic experts in loop and in action, right away.
- Reputational damage by a post or content or leak on social media
- Customer data breached and found on darkweb / social media
In both of these cases, the liability and its enforcement are clear and often huge. A legal option and a legal process should be kicking in as soon as any of these two are found and/or reported.
Darkweb monitoring and external monitoring, can add a dimension to your own internal monitoring and overall threat monitoring and threat management objectives.
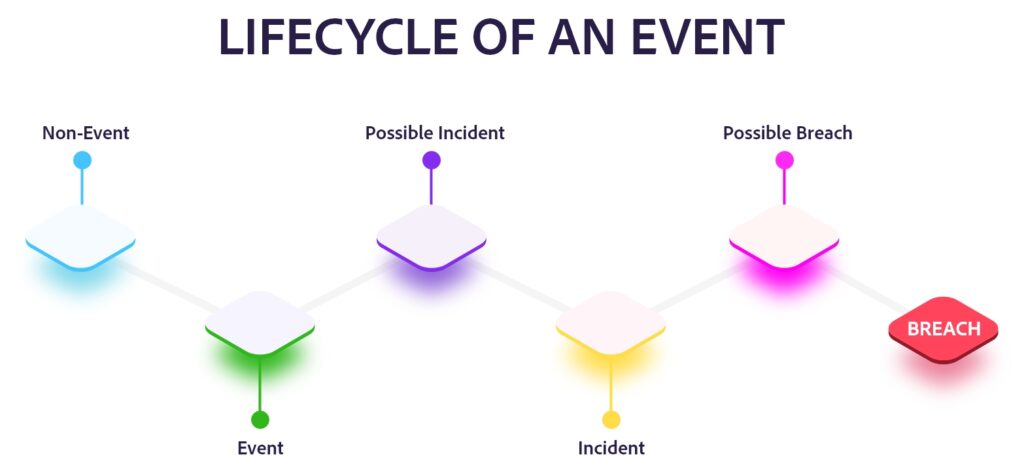
While SOC based monitoring, provides you with a view of what might be a threat elements within your own enterprise setup, darkweb & other external threat monitoring, provides you with information and intelligence, which is collected from outside, and, sometimes it is a lot more critical to act immediately upon, than, an internal alert.




Leave a comment: